Robtex
Robtex
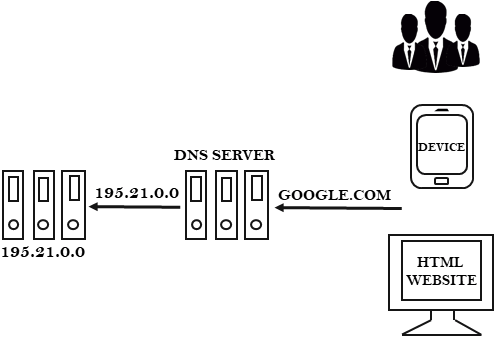
In this section, we are going to discuss how we can get comprehensive DNS information about the target website. Now we will discuss what DNS is. Suppose we type GOOGLE.COM in the URL, then it will be converted into an IP address using the DNS SERVER. It contains a number of records, and each record pointing to a different IP and a different domain. Sometimes, records point to the same IP. In general, they request the domain name, it gets converted into an IP address, and on the basis of address, the information needs to be stored somewhere. We will query the DNS SERVER and see what information we get through it. The process is illustrated in the given diagram:
We will use a website called Robtex (https://www.robtex.com/), and search isecur1ty.org. Now, just click on GO and select the first result on the website.
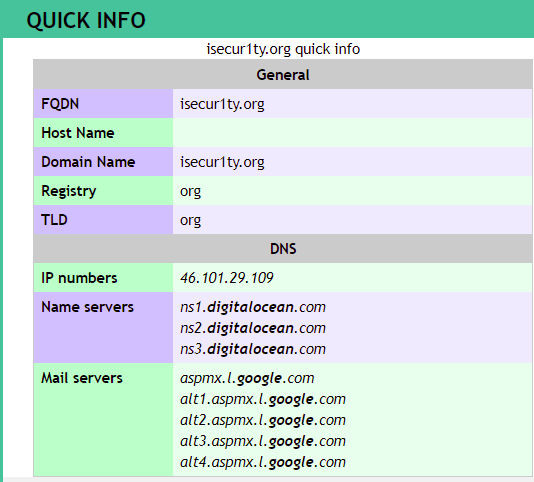
In the preceding screenshot, we get information about the website. We can see the DNS report, Name servers that have been used, and some Mail servers. We can also see the RECORDS that we were talking about and the DNS server as shown in the following screenshot:
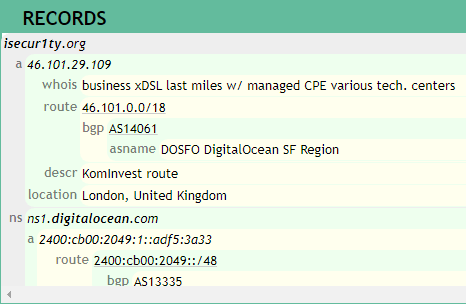
In the preceding screenshot, we can see all of these records. We can see the a record, the one that converts a domain name to an IP address, and if we remember, when we were performing DNS spoofing, we added an A record in our dns.conf and iter.conf files. The a record is used in DNS servers to link isecur1ty.org to its IP address. Again, there is another type of records. For example, we have ns record, which links the domain, the name server.
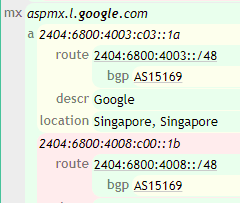
In the following screenshot, we can see the mx record, which links it to the mail server, and we can see that website uses a Google mail server, so it is probably using Gmail to provide mail services:
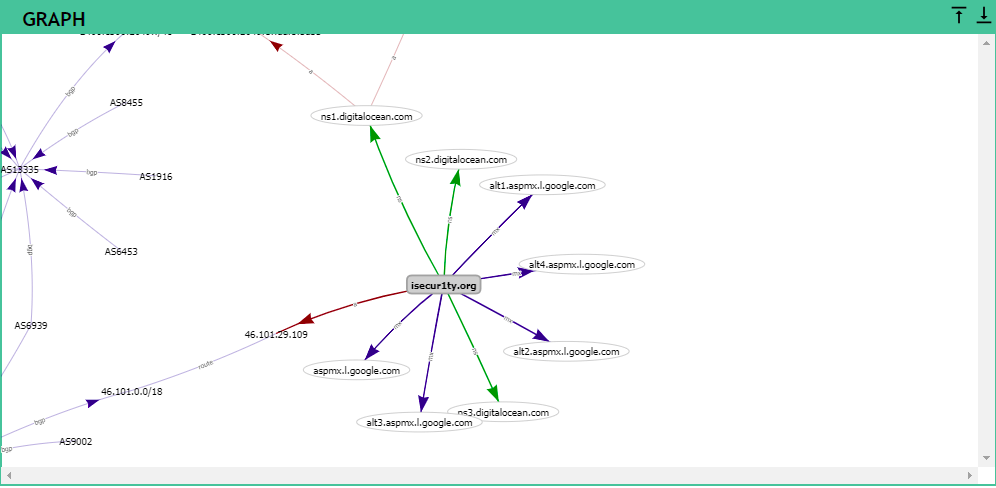
If we further scroll down, then we can see that we have a graph of how all of the services interact with each other, how the services use the records, and how they are translated into IP address as shown in the following screenshot:
In the Shared tab, we can see if any of these resources are being shared as shown in the following screenshot:
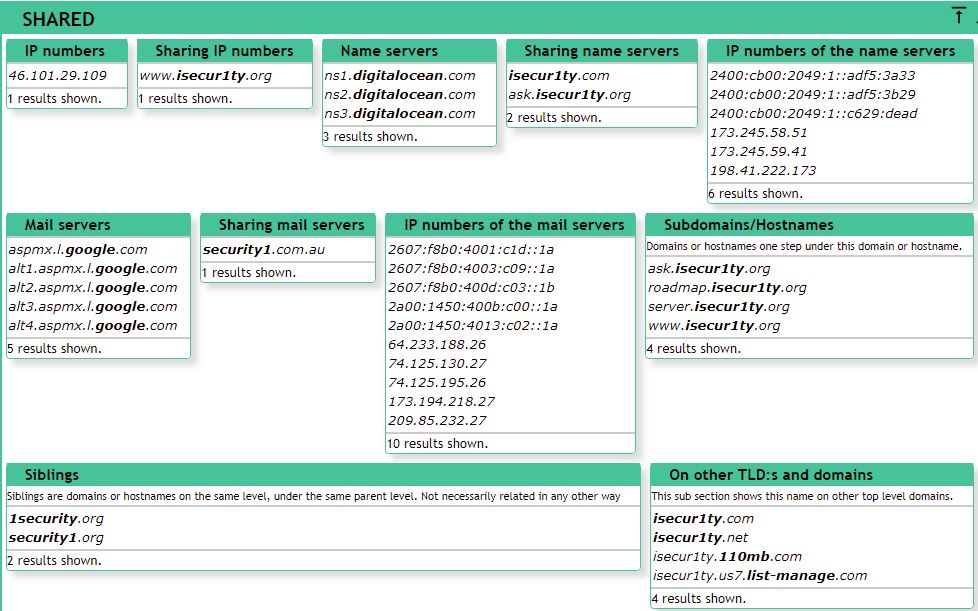
In the preceding screenshot, we can see that it is using three Name servers. We can see the Mail servers, and we can also see a number of websites pointing to the same IP address, and a number of domain name pointing to the same IP address. The preceding websites are stored on the same web server. Now, again there is more information about the name servers and websites that are Sharing mail servers. It does not mean that these websites are on the same server, but the most important thing is that we have the websites pointing to the same IP, which means that these websites exist on the same server. Now, if we gain access to any of the websites mentioned, it will be easy to gain access to isecur1ty.org.
Comments
Post a Comment