Nexpose analysis
Nexpose analysis
Once the scan is over, we are on the Asserts page. In the following screenshot, we can see that we have one asset scanned, and the asset is running on Ubuntu. The skill that we need to hack into this asset is Novice:
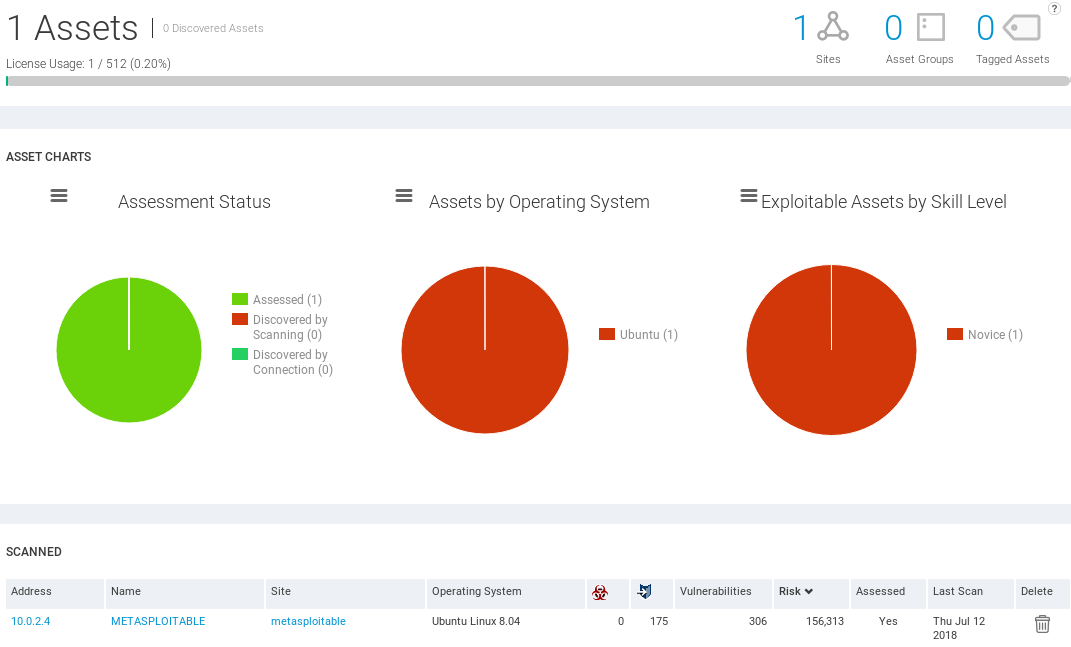
As we can see in the preceding screenshot, Nexpose shows us much more information than the Metasploit Community. Nexpose is a much more advanced vulnerability management framework.
We can see in the following screenshot, we scanned one target which is METASPLOITABLE, the site is Global, and it is running on Ubuntu Linux 8.04. We discovered no malware, 175 exploits, and 306 vulnerabilities. With Metasploit Community, we only discovered 1 exploitable vulnerability and 8 modules that can be used. But in Nexpose, we discovered 306 vulnerabilities. In this, we discovered many more vulnerabilities and exploits than Metasploit Community.
We can see that there is a risk factor. We can also see the Last time that the scan was done. If we scroll down, we are able to see the OPERATING SYSTEM that we discovered which is Ubuntu Linux 8.04. We can see the SOFTWARE that is installed on the target computer:
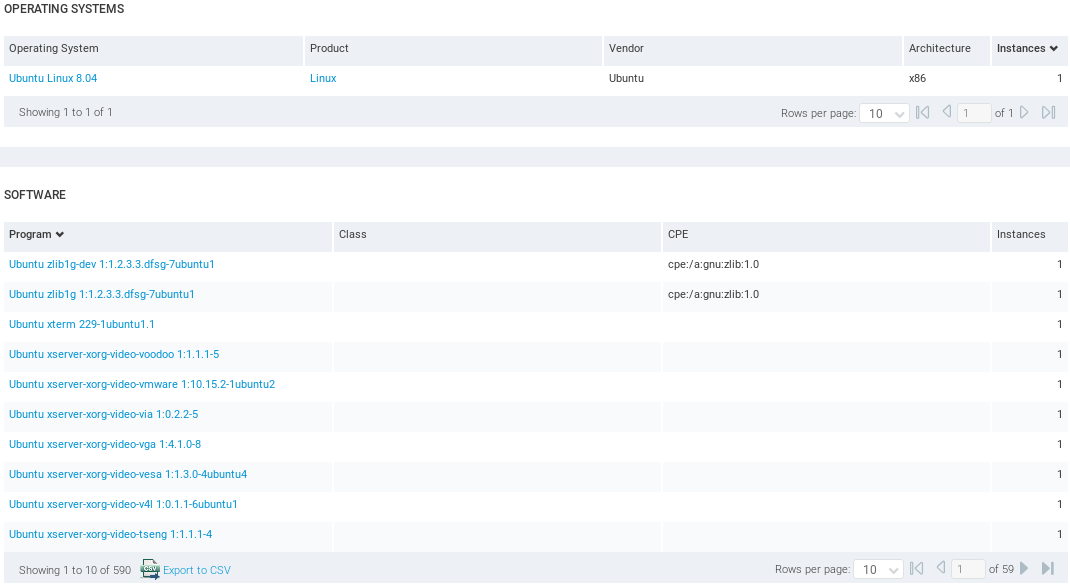
After we have managed to hack into it, it is very useful to find the local exploits that can be used to increase our privileges. For example, if we got a normal user and we wanted to become root, then we can use a local buffer overflow to increase our privileges or to do other kind of stuff. In post-exploitation, these are very useful.
If we go down, we are able to see the SERVICES that are installed on the target computer. We can see that the various services are running like HTTP, DNS, and so on:
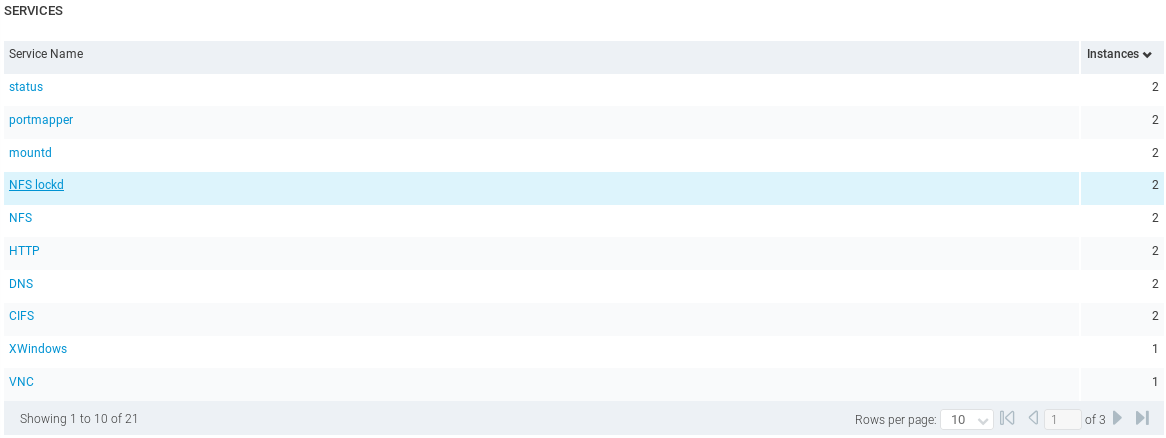
If we click on any of these services, we will see more information about them. For example, if we click on HTTP service, we will get a description about it, and the ports that are running on it. In the following screenshot, we can see that HTTP is running on port 80 and port 8180:
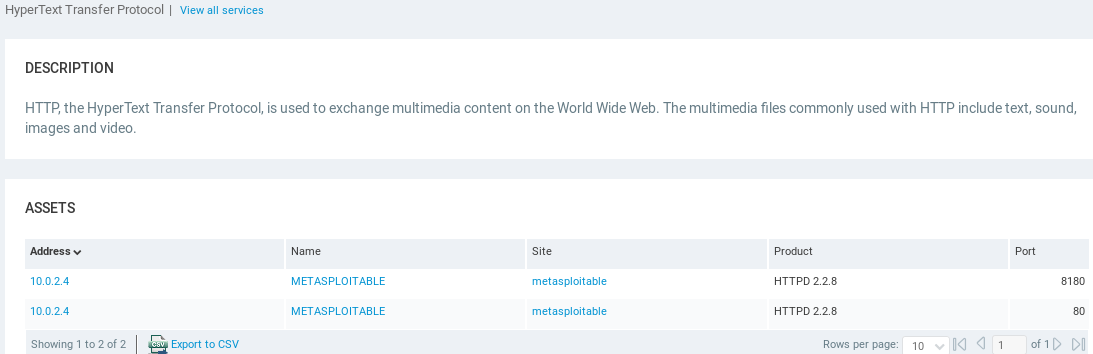
Now, let's scroll up, and if we want to have a closer look at the vulnerabilities, we can go to the Vulnerabilities page:
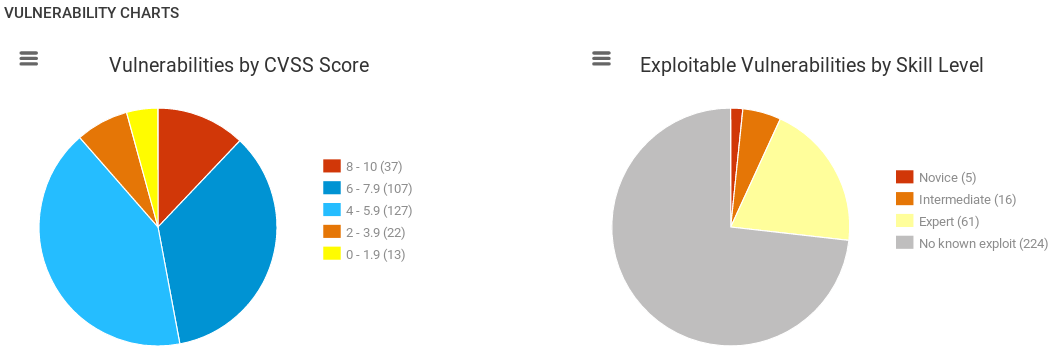
In the preceding screenshot, we can see that we have a graph about the vulnerabilities that were categorized based on the risk factor and based on the skill level in order to exploit these vulnerabilities. On the left side they are categorized based on risk factor, and on the right side, they are categorized based on the skill level. As we scroll down, we can see a list of all vulnerabilities, and we can switch between them using the arrows:
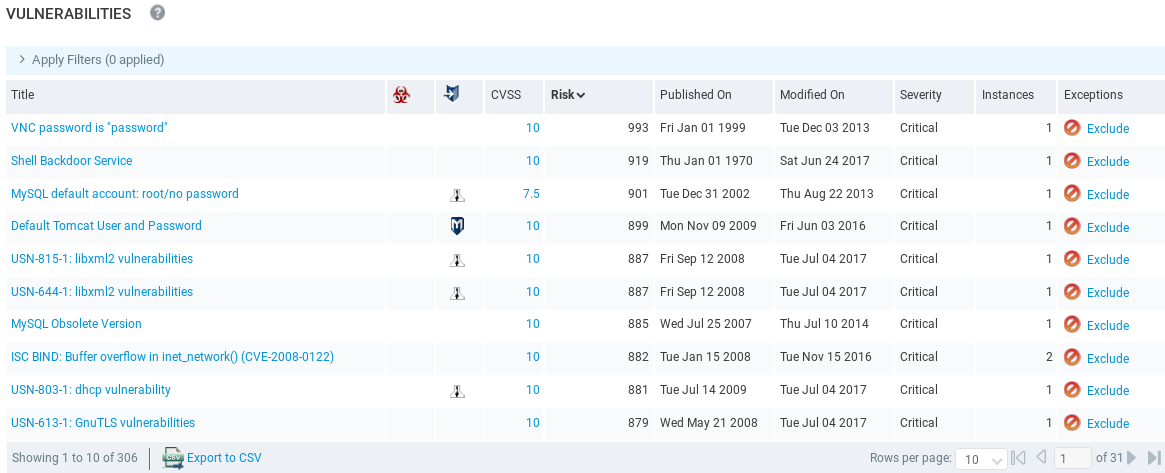
Again, if there is exploitation, we will see it under the exploit icon, and if there is any malware, we will see under the malware icon. Now, all of the top vulnerabilities listed don't have exploitation using a tool, but they are ordered based on the risk.
In the preceding screenshot, we can see that we discovered the VNC password is "password". We can go in and trying to connect using VNC. VNC is a service that is very similar to Remote Desktop. It will show us the Desktop, and it will allow us to gain full access to the target computer, just like Remote Desktop. It is telling us that the password for login is password. There is also a back door Shell Backdoor Service running, and we used that already.
Now, we are going to look at something that can be exploitable. We are going to click on exploit icon to order them by the exploit, and we can see that all of them have an M logo, which means that they can be exploited using Metasploit:
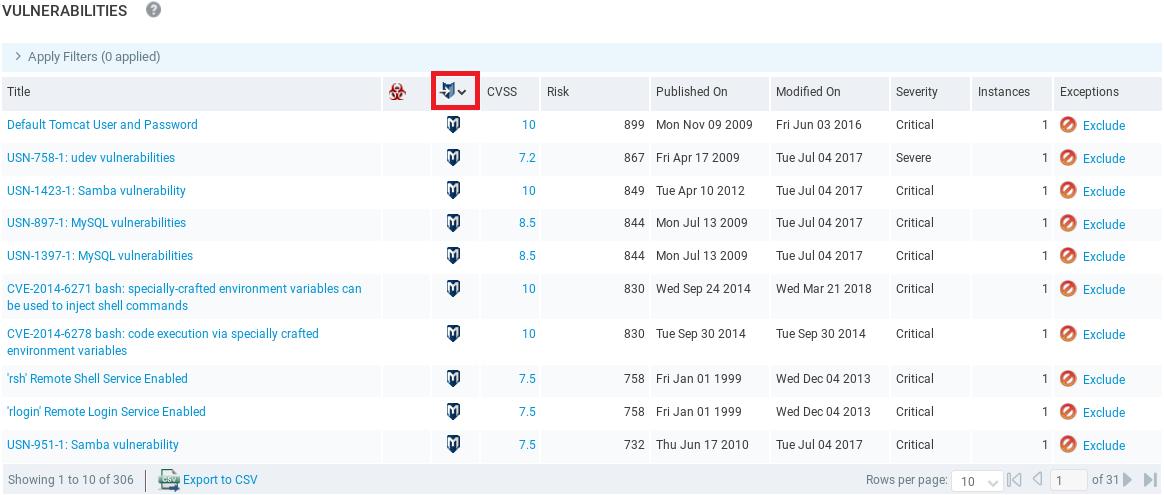
In the above screenshot, we have the Remote Shell Service and Remote Login Service that can be used, which we already had a look at. Now, we are going to click on something that we have not seen before, for example, Default Tomcat User and Password. In the following screenshot we can see a description of this vulnerability:
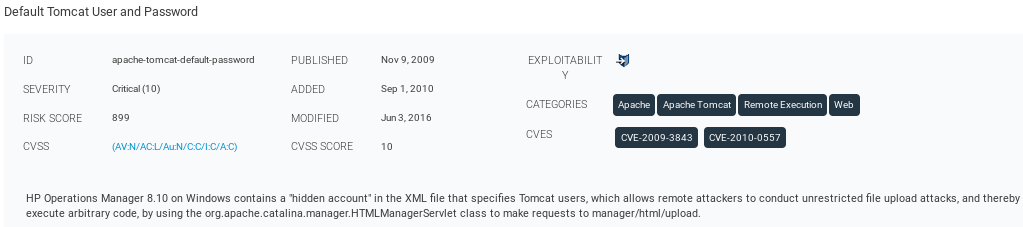
In the following screenshot, we can see the running port which is 8180, and we can see why it thinks that this particular target is vulnerable to this exploit:
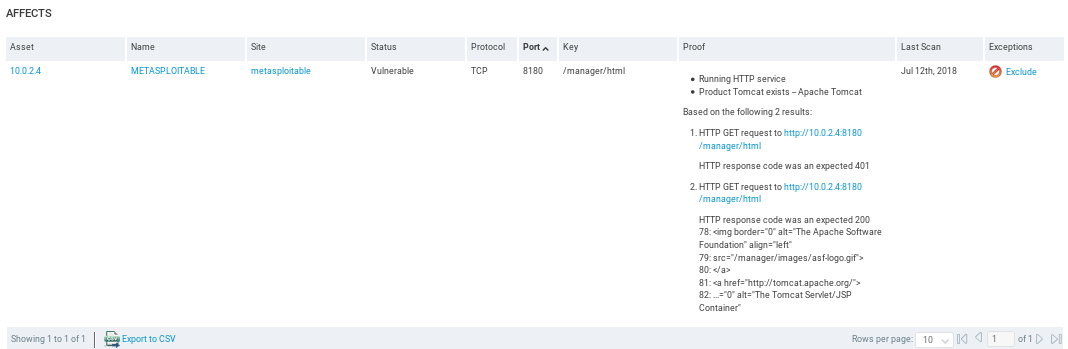
If we scroll down, it will show us how we can exploit it:
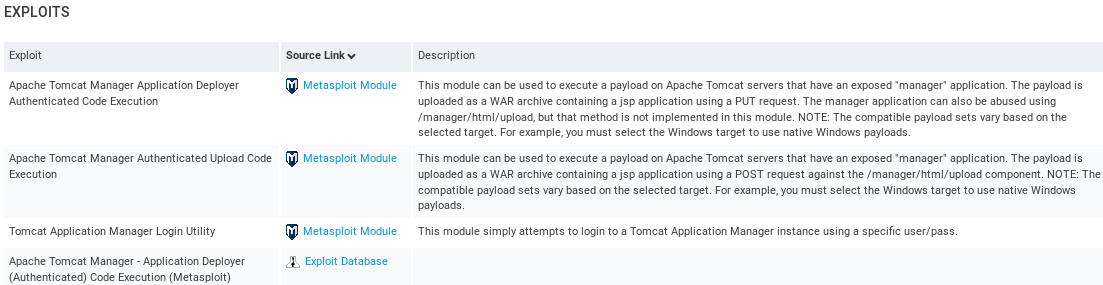
In the above screenshot, there are three different modules that can be used to exploit it, but it does not really have to exploit it. Sometimes we just see modules that can be used to verify the existence of this exploit. But these modules are associated with it, and if we click on any of the Exploit under the Source Link, it will take us to the Radip7 page that we used to see when we Googled stuff:
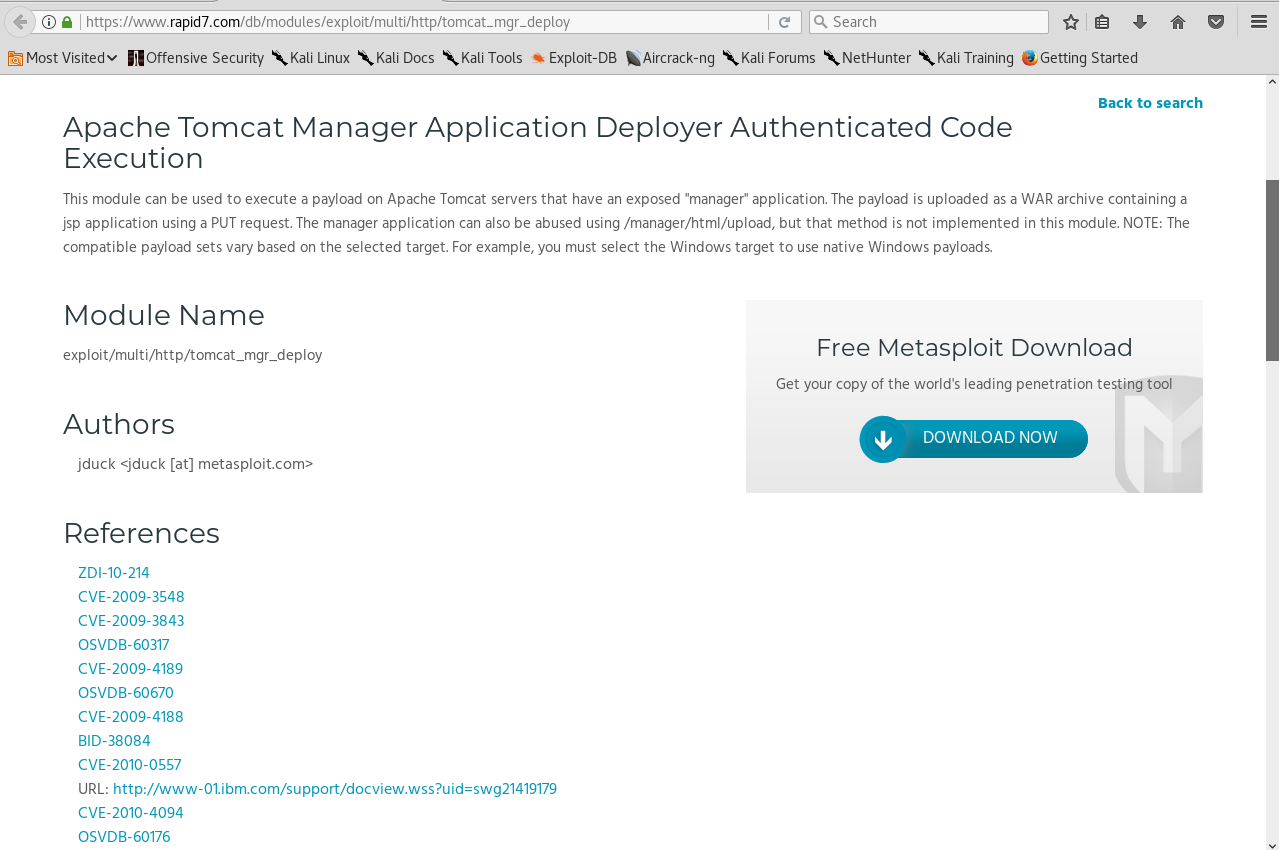
In the above screenshot, we can see the Module Name, which we can just copy and paste into Metasploit, where we can run show options and then use to exploit in the same way as we did in the Metasploit basic section. If we scroll down further, we can see the REFERENCES to the particular exploit:
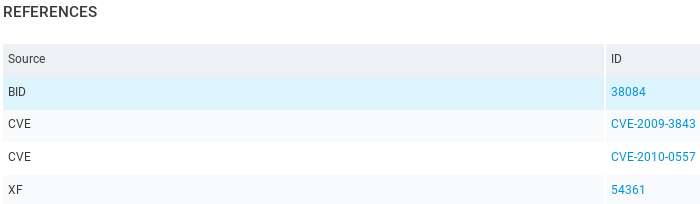
At the bottom, it will show us the REMEDIATIONS on how we can fix this exploit:
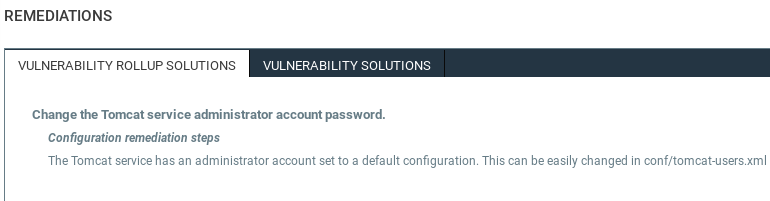
For this vulnerability, we will change the administrator password and not use the default configuration.
Now we are going to click on Reports tab to generate the reports for each scan that we do:
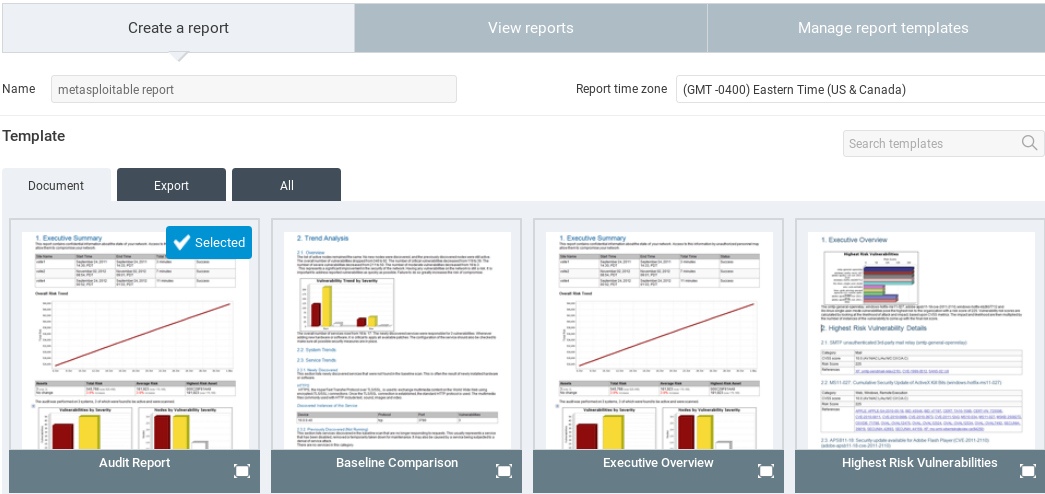
In the above screenshot, we can see that there are three different types of template for the reports. Inside Create a report, we can see that there is an Audit Report that has a lot of detailed information for the programmers. There is also Executive Report that contains less information and is mode of for the top-level people like managers that don't have much experience with technical stuff. We can select any template that we want and name it anything. In the preceding screenshot, we will call this report metasploitable report. If we scroll a little, we can select the format that we want:
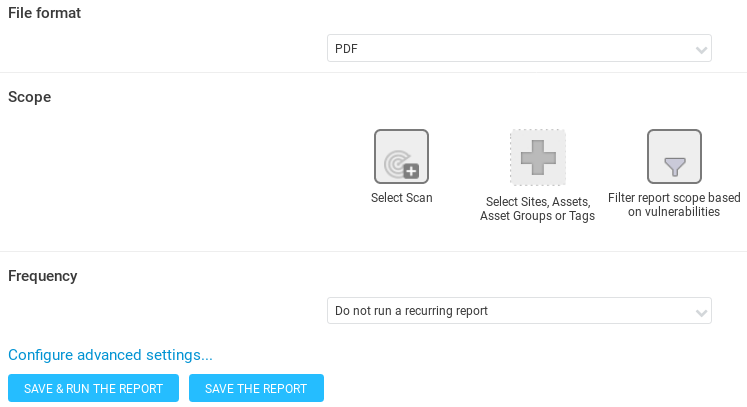
In the preceding screenshot, it is set to PDF. Now, we are going to click on Select Scan, then select our target scan that we want to generate a report for, and select metasploitable:
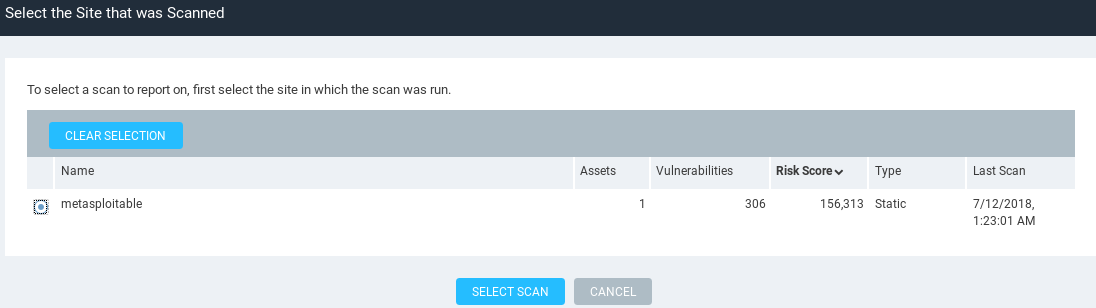
Now, click on SAVE & RUN THE REPORT to generate the report.
We can also schedule an automatic report each time a scan is done. For example, if we are scanning every week, we can also generate a report every week. Now, we can just download the report by clicking on the report, and let?s see what it looks like:
In the above screenshot, we can see that it has the date, it has the title, it has all the exploits that have been found, but this is the executive report. It contains small details about the exploits and more graphical stuff to show the executives the risks that have been found and how critical they are:
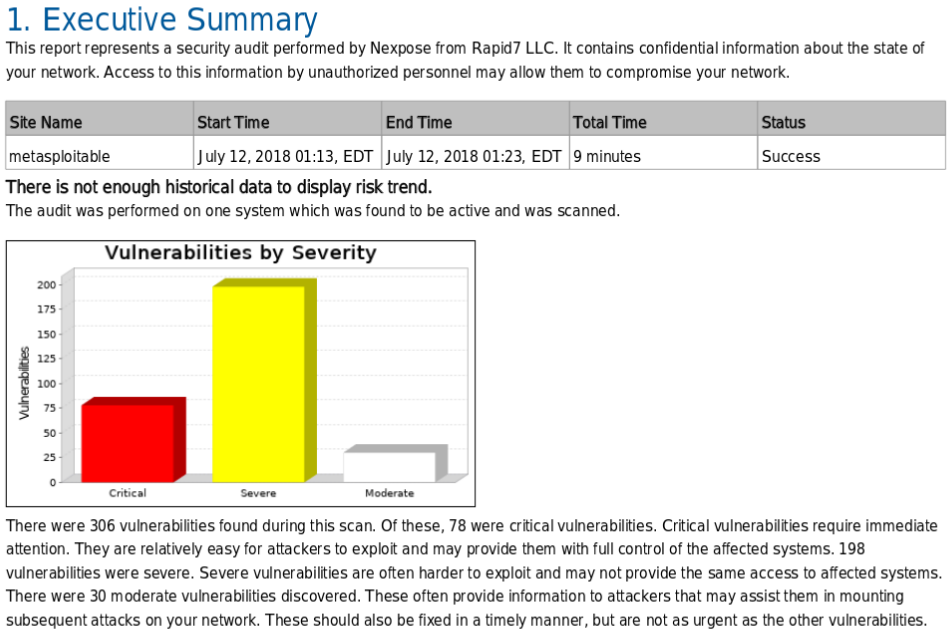
In the above screenshot, we can see that Nexpose shows us much more detail and it is much more advanced. It is directed towards bigger infrastructure, bigger companies, where we need always to make sure everything is up to date, everything is installed, and there are not any exploits.
Comments
Post a Comment