Analysing Discovering Files
Analysing Discovering Files
In the following screenshot, we can see the result that the dirb tool was able to find a number of files. Some of the files we already know:
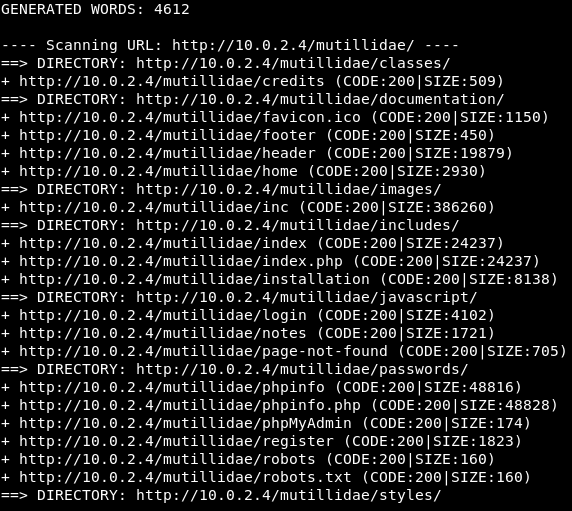
In the following screenshot, we can see that favicon.ico is just an icon. The index.php is the index that we usually see. The footer and header are probably only style files. We can see that we discovered a login page.
Now, we can find the target's username and password by exploiting a really complex vulnerability. Then we will end up not being able to log in because we could not find where to log in. In such cases, tools like dirb can be useful. We can see that the phpinfo.php file is usually very useful because it displays a lot of information about the PHP interpreter running on the web server, and as we can see in the following screenshot, the file contains a lot of information:
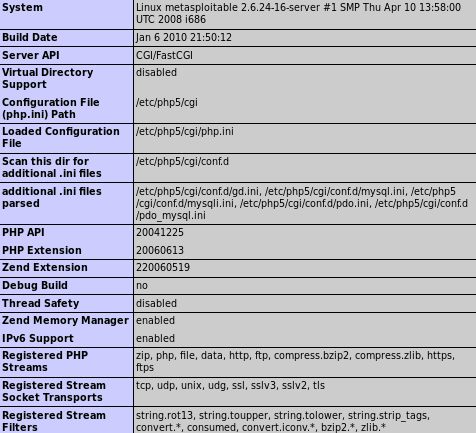
The preceding informations are useful. Using this information, we can get to know some of the directories. From the preceding screenshot, we can see that it is running on php5. .cg1 file stored the configuration. .ini files are usually the config file for PHP, so we can see all the places where they are stored.
When we further scroll down, we will see the installed permissions. We will also see that it has MySQL, so it is using MySQL:
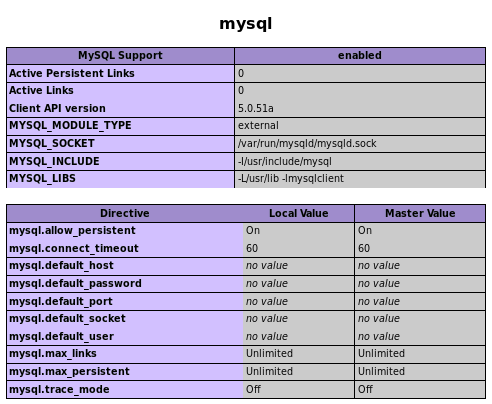
In the preceding screenshot, we can see the directories where different types of configurations are stored. We can also see the modules and extensions that are being used with PHP, so the phpinfo.php file is very useful. In the following screenshot, we can see that we managed to find where the phpMyAdmin login is, and that is basically the login that is used to log in to the database:
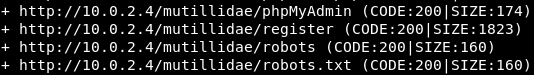
robots.txt file is another very useful file, which tells search engine such as Google, how to deal with the website. Hence, it usually contains files that we don't want the website or Google to see or to read. Now, if we can read the robots.txt file, then we will be able to see what the web admin is trying to hide. In the following screenshot, we can see that the web admin does not want Google to see a directory called passwords, and it doesn't either want us to see a file called config.inc. Neither it wants to see these other files:
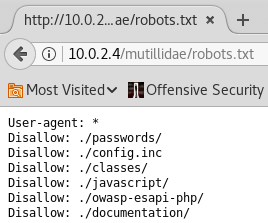
Now, let us see the ./passwords and ./config.inc files in the following screenshot:
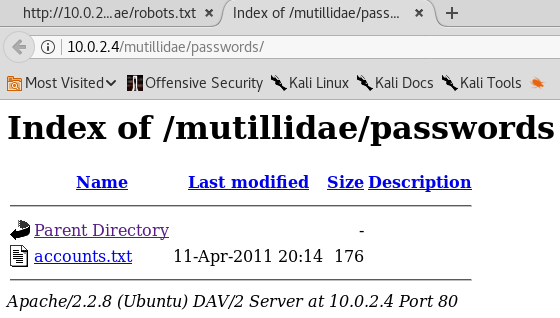
In the preceding screenshot, we can see that there is accounts.txt file, and clicking on the file, we can see that we have got some usernames and passwords. So, we can see that there is a admin user, with the adminpass password and we can see that we have a password for the adrian user, which is somepassword. In the following screenshot, we can see that we managed to find usernames and passwords:
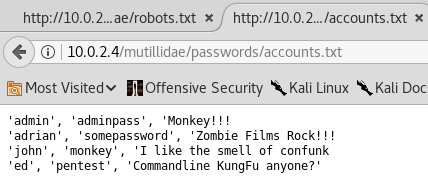
Now, we are still not sure what the preceding usernames and passwords are for, but we are sure that we were able to find very useful information. Config.inc file is another useful file. In the following screenshot we can see that we have information that allows us to connect to the database, because they have $dbhost, $dbuser, $dbpass, and $dbname parameters:
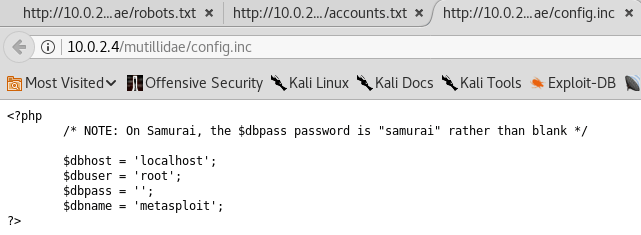
In the preceding screenshot, we can see that the username is root and the password is blank, so we can go ahead and try to connect to the database based on the commands from the preceding screenshot, and then we should be able to get access to the database.
Also, we are still not sure where we can use them, but we can add them to a list to try to log in to the admin, or just store them in a list so that we can use them if we carry out a brute-force attack.
Comments
Post a Comment